Being an EUC administrator you often come across requests to update applications in your environment for various reasons like, vulnerabilities associated with current version, newer version has some bug fixes and more reliable etc.
Every application has its own updating methods and challenges associated with it. However, when it comes to updating VPN client, major challenge is to ensure any active VPN connection is not disconnected during update process as this may potentially cause disruption to other applications/tasks dependent on VPN connection and may subsequently lead to user data loss.
In this article I am going to demonstrate how to update VPN client GlobalProtect by Palo Alto Networks using SCCM without disconnecting any ongoing VPN connection. The trick here would be to ensure GlobalProtect VPN client is updated only when no active VPN connection is found. With some adjustments according to behavior of your VPN software and organizations need, method described here might be useful to other VPN software as well.
This post in written with assumption that Cloud Management Gateway or Internet based client Management is enabled for the devices to get policies and required content when they are not connected to VPN.
I would also like to mention here that GlobalProtect Agent can also be upgraded via Palo Alto Firewall. GlobalProtect Agent Upgrade Process can be “Allow with Prompt” (end-user will be prompted for upgrade upon VPN connection) or “Transparent” (upgrade will happen without user interaction). Additional details can be found here:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClkSCAS
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g0000008U4ICAU
Contents of this article
- Custom Global Condition to detect GlobalProtect VPN Client Status
- Create SCCM application update package for GlobalProtect
- Update GlobalProtect VPN client using SCCM custom task Sequence
- Conclusion
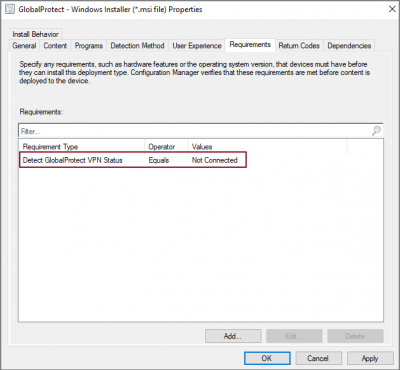
Custom Global Condition to detect GlobalProtect VPN Client Status
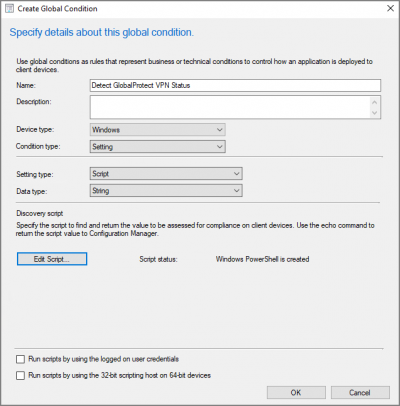
Launch SCCM console and navigate to Software Library -> Application Management -> Global Conditions. On the Home tab, in the Create group, choose Create Global Condition to create Global Condition with following properties:
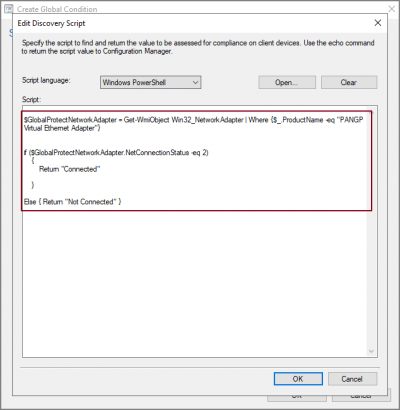
In Discovery script section click “Add Script” Button and following PowerShell script. Click OK to exit from Edit Discovery Script Window.
$GlobalProtectNetworkAdapter = Get-WmiObject Win32_NetworkAdapter | Where {$_.ProductName -eq "PANGP Virtual Ethernet Adapter"}
if ($GlobalProtectNetworkAdapter.NetConnectionStatus -eq 2)
{
Return "Connected"
}
Else { Return "Not Connected" }Click OK to complete Global condition creation.
If you are using other VPN software like Cisco Anyconnect, Pulse Secure, Zscaler Private Access, SonicWall Global VPN Client etc. following PowerShell command is to identifying network adapter name to be used to create or modify global condition discovery script to meet your requirement.
Get-WmiObject Win32_NetworkAdapter | select ProductName
Create SCCM application update package for GlobalProtect
Get copy of GlobalProtect MSI installer from Palo Alto VPN Gateway portal or contact Palo Also support/Network administrator for the same. MSI installer of GlobalProtect, it takes care of uninstalling older version and installs new version. Here is the link on how to download GlobalProtect.
Open Configuration Manager Console and Navigate to Software Library -> Application Management -> Applications.
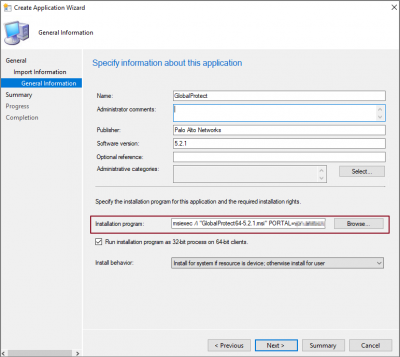
Review the application information and click Next. Enter general information about the application like, Name, Publisher, Software version etc.
Installation program can also be modified here to include additional MSI install properties. Commonly used MSI properties in case of GlobalProtect is to configure the portal address.
msiexec /i “GlobalProtect64-5.2.1.msi” PORTAL=portal.company.com /qn /norestart
GlobalProtect MSI installer provides several customizable properties, listed here.
GlobalProtect application update package in now ready to be deployed to devices. Needless to mention here that package content need to be available on cloud DP or DP enabled Cloud Management Gateway so that devices on the internet can download this package when they are not connected to VPN.
Post deployment, devices where GlobalProtect VPN is “Connected” will be listed under “Requirements Not Met” tab of Deployment status.
At next “Application Deployment Evaluation Cycle” defined in the SCCM client setting, requirements will be checked again and if met i.e., active VPN connection was not found then GlobalProtect will be deployed.
Update GlobalProtect VPN client using SCCM custom task Sequence
To get better results you would want to check VPN connection status as frequently as possible instead of waiting for next “Application Deployment Evaluation Cycle”, so that an attempt to update GlobalProtect VPN client can be made as soon as possible.
To overcome this limitation of standalone GlobalProtect application package, we will be taking help of SCCM custom task sequence to deploy GlobalProtect update application package. With SCCM Task Sequence we have advantage of creating recurring deployment. Please go through this Microsoft article to understand custom task sequence and how to create one.
Here is how task sequence I had create for Global Protect looks like:
Step 1 : Set _SMSTSLastActionSucceeded = False
“Run Command Line” task sequence step where command cmd /c exit 1 is run which will fail and subsequently task sequence engine will set _SMSTSLastActionSucceeded = False.
I have also set this step to continue error so that this does not halt task sequence progress.
_SMSTSLastActionSucceeded is built-in SCCM task sequence variable which holds status of previous task sequence step. Further details about this and other task sequence variables can be found here
Step 2 : Update - GlobalProtect 5.2.1
“Install Application” task sequence step where we will be performing update of GlobalProtect client. Here include SCCM application created for GlobalProtect update in earlier step.
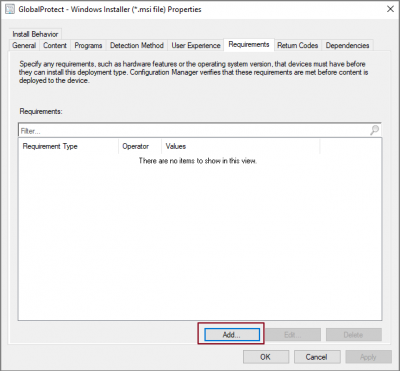
In the options tab following WMI query-based condition is added to ensure this step is executed only when GlobalProtect VPN connection is NOT active.
SELECT * FROM Win32_NetworkAdapter WHERE ProductName = ‘PANGP Virtual Ethernet Adapter’ AND NetConnectionStatus != 2
This query uses ProductName and NetConnectionStatus properties of WMI class Win32_NetworkAdapter to determine GlobalProtect VPN connection status. Further details about Win32_NetworkAdapter class can be found here
If this step is executed successfully then task sequence engine will set _SMSTSLastActionSucceeded = True. In case this step is skipped due to condition not being satisfied Task Sequence engine will honor value we had set earlier i.e. _SMSTSLastActionSucceeded will remain False.
Step 3 : Fail Task Sequence if Required
Objective of this step is to fail the task sequence if previous step “Install – GlobalProtect 5.2.1” is skipped i.e. GlobalProtect was not updated due to an active VPN connection. This is achieved by running command cmd /c exit 1 when value of _SMSTSLastActionSucceeded remains false, this condition is defined in the Options tab.
If GlobalProtect was successfully updated in the previous step, then this step is skipped because task sequence engine will set “_SMSTSLastActionSucceeded = True” after executing Step 2.
Flowchart of how it is going to work:
Next step is to deploy this task sequence to device collection as mandatory deployment in recurring mode. Attempt to update GlobalProtect VPN client will be made on regular interval defined in recurring deployment schedule. Please ensure Rerun behavior is set to “Rerun if failed previous”, here I have set recurrence schedule for every 3 Hrs. please make sure to modify this to the duration feasible to your organization.
Conclusion
In this post I talked about two methods – 1) Standalone application package that relies on Global Condition to check VPN connection status 2) Custom Task Sequence using GlobalProtect application package with recurring deployment. Another possibility I touched upon in introduction section is to push out GlobalProtect upgrade via Palo Alto Firewall. In some cases you might have go with combination of methods to achieve to a better success rate. It’s always recommended to read vendor documentation to understand best practices and methods to update the application. Its quite possible they have some command, switches etc. to simplify the update process. For example, I was working on Zoom client update request with obvious requirement to ensure any ongoing meeting should not be disconnected during the update. While reading Zoom client documentations I came across this MSI switch MSIRESTARTMANAGERCONTROL=”Disable” when used instructs the installer to wait until in-progress meeting ends before installing.
I hope this post has been helpful to you. Please feel free to reach out if you have any further questions/comments/feedback.
Thank you.





















Very nicely explained , with crisp content.
This will be really useful for many.
Thank you.
Thanks for taking time to read this article and your comment. Happy to know that post will be helpful.
Thanks for taking the time and effort to publish it. It is very helpful and I really appreciate it. Do you have direct contact?
Thank you very much. You can reach me at Premndra@gmail.com
Hi Premendra,
Do you have any idea how can compare the globalprotect version for sccm deployment? any less than deployment version will be ignore.
TQ
Hi Justin,
Globalprotect version can be compared via SCCM application detection method, this can be based on a Registry key or file version.
File version to be checked – C:\Program Files\Palo Alto Networks\GlobalProtect\PanGPA.exe
Registy Path – HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{PRODUCTGUID}\DisplayVersion
You may also use the above conditions to execute/skip any task sequence step.
Hope this helps.
I’m getting an invalid WMI Query when trying to use:
SELECT * FROM Win32_NetworkAdapter WHERE ProductName = `PANGP Virtual Ethernet Adapter’ AND NetConnectionStatus != 2
Should this be the case?
Hi Tyler,
Looks like a syntax error in WMI query, ProductName value should be in single quotes. In your case, ProductName value is starting with a backtick (`) not single quote.
Give this a try, it should work.
This fixed it … I typed it manually and it takes perfectly. I guess the copy / paste didn’t work right.
Good to know that you got this working 🙂
Hi Premendra,
This was a great guide as I’m currently working on upgrading all of the GP clients in our environment. However after testing this against 25 systems in our environment, 2 of them restarted after the application was successfully upgraded without any warning to the user.
I have tried the following commands, with the same behavior:
msiexec /i “GlobalProtect64-5.2.7.msi” /quiet /norestart /L*V “C:\windows\temp\GlobalProtect.log”
msiexec /i “GlobalProtect64-5.2.7.msi” /qn /L*V “C:\windows\temp\GlobalProtect.log”
Within the Task Sequence Deployment Log, this is the detail of the message: The Task Sequence execution engine performed a system reboot initiated by the action (Install Application) in the group ().
Do you have any idea why this would be happening on a very small subset of systems, or what could be added in the Task Sequence to ensure the system doesn’t restart after a successful upgrade? Thanks!
Hi Premendra,
Great post, this is working great however I’m currently running into a small issue with some computers restarting after the application is successfully upgraded without a notification to the user.
I have tried the following install strings:
msiexec /i “GlobalProtect64-5.2.7.msi” /quiet /norestart /L*V “C:\windows\temp\GlobalProtect.log”
msiexec /i “GlobalProtect64-5.2.7.msi” /qn /L*V “C:\windows\temp\GlobalProtect.log”
The status message that appears in the Task Sequence status message query is: The Task Sequence Execution engine perfromed a system reboot initiated by the action (Install Application) in the group ().
Do you know of a way to ensure the system doesn’t restart, or know of a way to modify the Task Sequence by maybe adding a restart step with a timeout or soemthing like that? I want to ensure my users systems don’t get restarted.
Thanks!
Hi Justin,
Glad to know this post has been helpful for you.
Regarding the restart issue with some computers, please ensure to select “No specific action” under “User Experience” tab of deployment type properties. By default “Determine behavior based on return codes” is selected which can cause restart if application enforcement exits with a return code that requires a reboot. Please review appenforce.log to confirm if this is happening in your case.
Thank you!
Only admintration with CGM work? Would not it be right to use specific boundaries for VPN IP addresses? That is the client behind VPN only works with cmg?
This would be absolutely right to assign CMG to a boundary group consisting of VPN IP ranges to ensure VPN clients work with CMG.
WMI is being deprecated. A better way to get the network adapter is:
$GlobalProtectNetworkAdapter = Get-CimInstance Win32_NetworkAdapter -Filter “ProductName = ‘PANGP Virtual Ethernet Adapter'”
if ($GlobalProtectNetworkAdapter.NetConnectionStatus -eq 2)
{
Return “Connected”
}
Else { Return “Not Connected” }
Hi John,
This would be a better way of getting adapter status, I am with you on this.