In this post I will be focusing on ways to disable NetBIOS over TCP/IP. If you wish to learn more about NetBIOS and vulnerabilities/risks associated when NetBIOS over TCP/IP remains enabled, following are some great articles.
https://support.microsoft.com/en-in/help/204279/direct-hosting-of-smb-over-tcp-ip
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2000/ms00-047
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2003/ms03-034
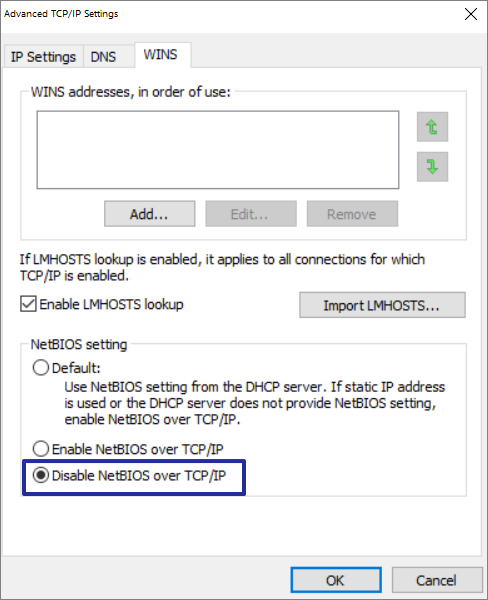
How to Disable NetBIOS over TCP/IP
There is no direct out-of-the-box GPO setting, configuration policy which can be applied to configure this setting. Also, this must be done for all network interfaces. Therefore, the solution must be dynamic, i.e. If setting is done or one interface; say for onboard Network interface and later if we connect a docking station or USB-C/Thunderbolt ethernet adapter, or even VPN application also create their own virtual network adapter. They won’t get it unless the solution is dynamic in nature. Solution should check periodically and set this setting for any newly attached NICs.
Now, lets talk about the solution and then we will discuss how to make this solution a dynamic one with tools we have at our disposal. NetBIOS over TCP/IP can be disabled via registry, here is the path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NetBT\Parameters\Interfaces\ TCPIP_{GUID}Each TCPIP_{GUID} represents a network adapter. Under TCPIP_{GUID} Key,setting value of NetbiosOptions to 2 will disable NetBIOS over TCP/IP for a Network adapter. NetbiosOptions is set to 0 by default.

Here is the PowerShell script which will set NetbiosOptions to 2 for all network adapters present. Now onwards let’s refer to this script as Remediation Script as this remediates the vulnerability by disabling NetBIOS Over TCP/IP.
Set-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions -Value 2


Next, we will talk about methods to execute Remediation script periodically so that any newly detected network adapter can also get this setting.
I am going explain how to make use of following tools to execute remediation script:
- Intune Win32 Apps
- SCCM Application
- SCCM Configuration Item and Baseline
- Group Policy (Startup/Logon script and Group policy preferences)
Intune and SCCM based methods don’t require device be corporate network or connected to VPN. Intune natively manage devices over the internet. SCCM also support for managing devices over the internet provided features like Internet based client management (IBCM) or Cloud Management Gateway are configured to extend the reach over the internet clients. Intune and SCCM are capable of managing Azure AD joined, Hybrid Azure AD joined as well as AD joined devices.
Depending on the Co-management workload delegation between SCCM and Intune defines how Intune Win32 App, SCCM application and Configuration Baseline can be deployed to co-managed devices.
Group policy based method on the other hand require devices to be member of Active Directory Domain and connected to corporate network or VPN. Needless to mentioned, this is not an optimal solution considering present day’s cloud first approach and most of the applications and services do not require corporate network connectivity directly or via VPN.
Intune Win32 App
PowerShell script to disable NetBIOS over TCP/IP can also be deployed as an Intune App. We will be using Microsoft Win32 Content Prep Tool (IntuneWinAppUtil.exe) to pre-process and generate .intunewin file which can be then deployed as Win32 App using Intune. Please refer to this link to download and get more information about IntuneWinAppUtil.exe
Here are the steps:
Save Remediation Script to a ps1 file, say DisableNetBIOSverTCPIP.ps1
In the same directory, create another file DisableNetBIOSverTCPIP.cmd to which will be used to launch PowerShell script
powershell.exe -executionpolicy bypass -command "& '.\DisableNetBIOSverTCPIP.ps1' 1"
We would need some more files here which will be used to uninstall this app
Uninstall_DisableNetBIOSverTCPIP.ps1 with following content
set-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions -Value 0
Uninstall_DisableNetBIOSverTCPIP.cmd with following content to launch Uninstall_DisableNetBIOSverTCPIP.ps1
powershell.exe -executionpolicy bypass -command "& '.\Uninstall_DisableNetBIOSverTCPIP.ps1' 1


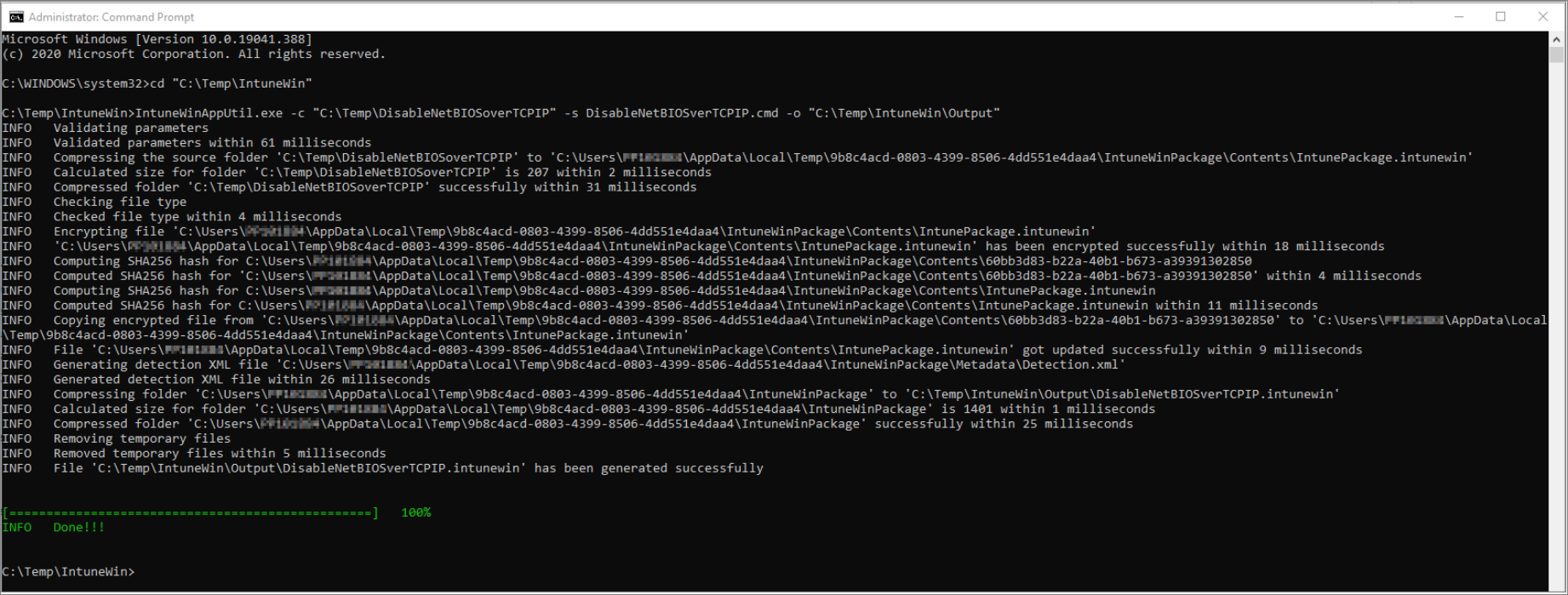
Download and save IntuneWinAppUtil.exe tool and Launch admin command prompt -> Navigate to location where IntuneWinAppUtil.exe is saved and type this command
IntuneWinAppUtil.exe -c "C:\Temp\DisableNetBIOSoverTCPIP" -s DisableNetBIOSverTCPIP.cmd -o "C:\Temp\IntuneWin\Output"


.intunewin file has been created


Let us go to Intune portal and create Win32 App using DisableNetBIOSverTCPIP.intunewin file
Go to Intune Portal -> Apps -> Windows Apps -> Select Windows app (Win32)
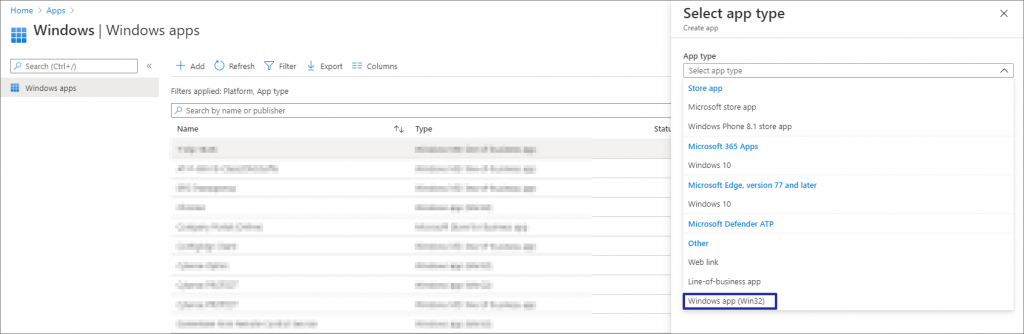


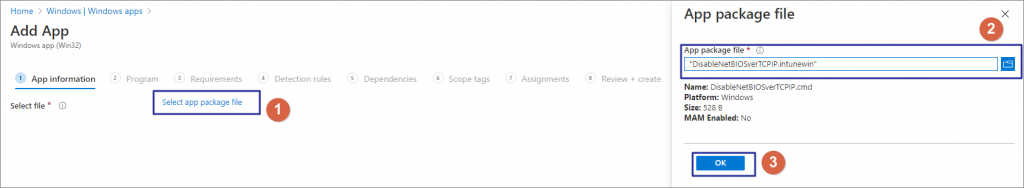
Browse and select DisableNetBIOSverTCPIP.intunewin


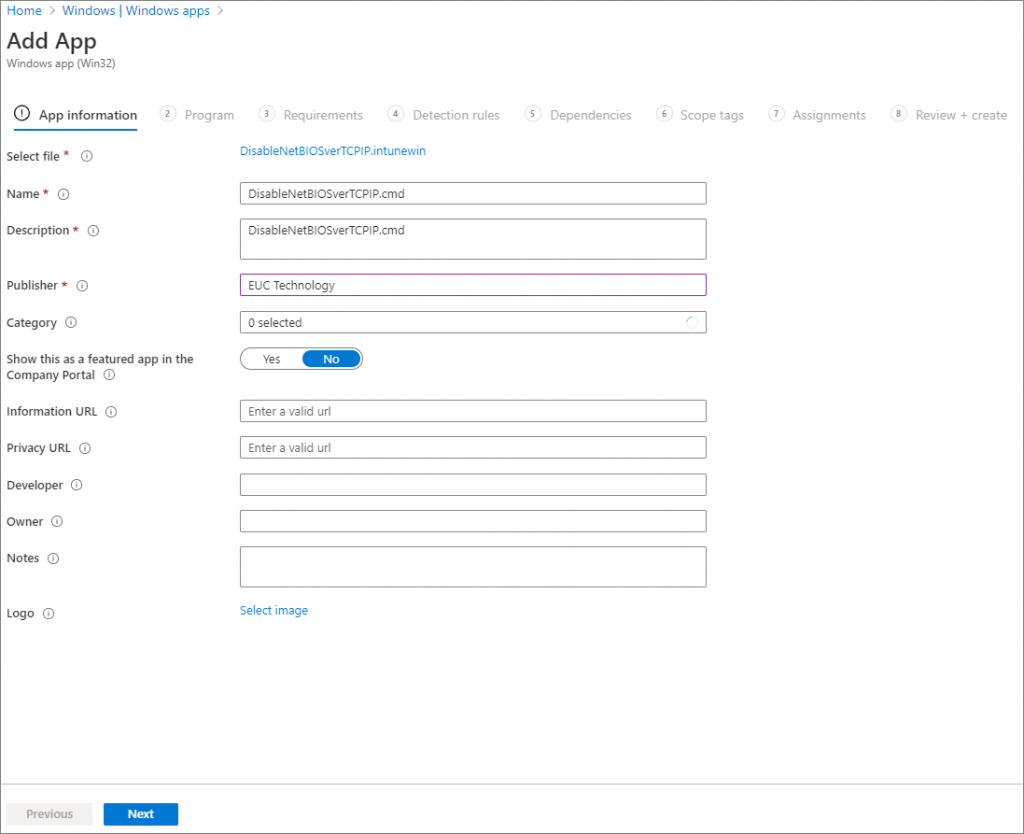
Intune portal will process the file and auto-populate some of the app information, here if you wish some more details can be added.


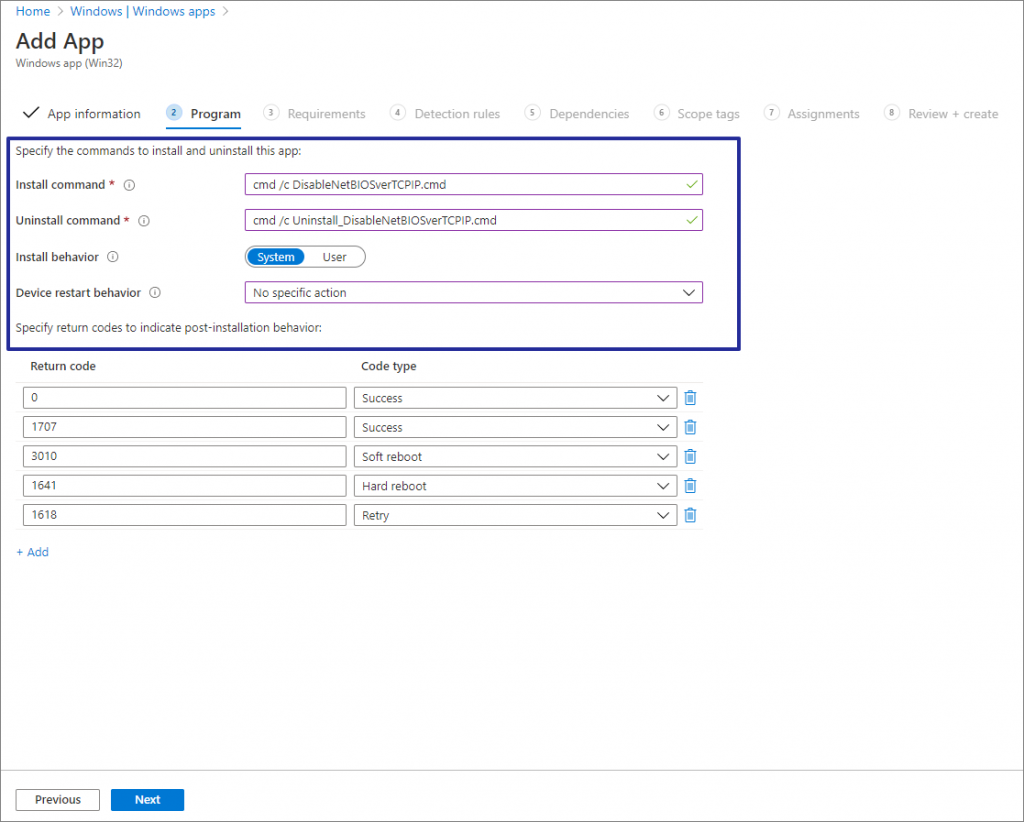
Provide install and Uninstall commands, install be behavior will be System. Set Device Restart behavior to “No Specific Action”, click Next


Provide requirements for this application, Next.
On Detection Rule page, select “Use custom detection script” and upload script file. Save following script as ps1 and upload as detection script -> Click Next
$NetbiosOptionsVlaues = Get-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions
$Counter = 0
Foreach($NetbiosOptionsVlaue in $NetbiosOptionsVlaues )
{
if($NetbiosOptionsVlaue.NetbiosOptions -ne 2)
{
$Counter+=1
}
}
if($Counter -eq 0)
{
Write-Host "Detected"
exit 0
}
else { exit 1 }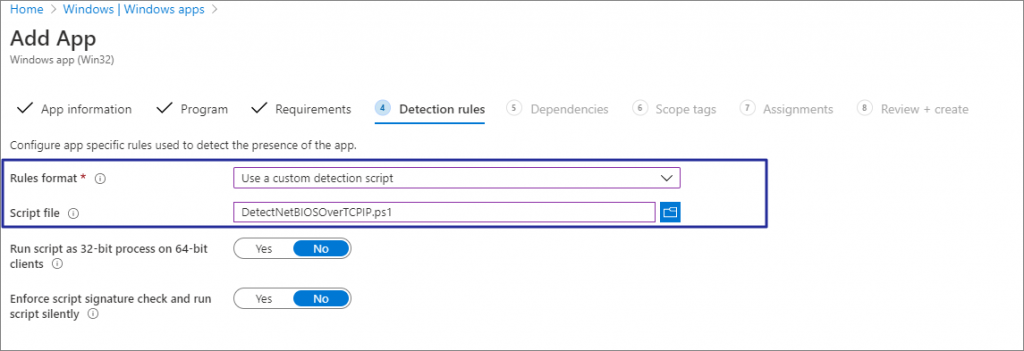


Assign this App to a group as Required install to make sure no user intervention is required -> click Create
When device sync happens and this app will be enforced if not detected. Intune enrolled Windows devices sync every 8 Hrs. by default.
SCCM Application
Save Remediation PowerShell script in PS1 file (Say DisableNetBIOSoverTCPIP.ps1) and utilize the same to create and SCCM application. Installation program would be:
Powershell.exe -ExecutionPolicy Bypass -file DisableNetBIOSoverTCPIP.ps1 -windowstyle hidden
Here we cannot use Registry, File or Windows Installer rule as detection method. Custom script will be used as detection method instead.
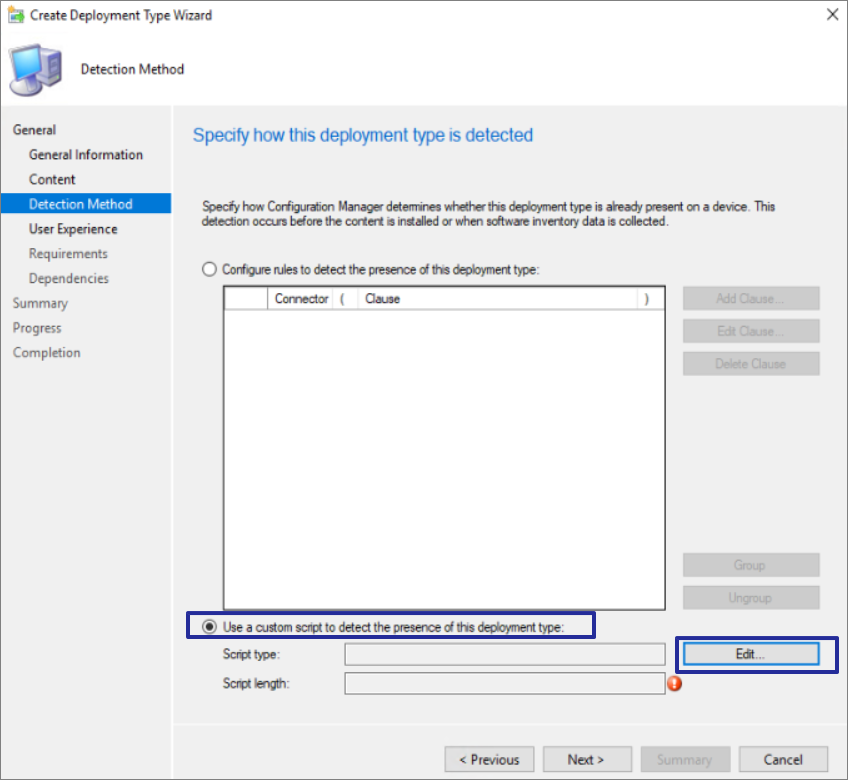


Here is the script I am using, this script checks NetbiosOptions value for each network adapter and desired value not found if not found for any of the network adapter, says application not detected.
$NetbiosOptionsVlaues = Get-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions
$Counter = 0
Foreach($NetbiosOptionsVlaue in $NetbiosOptionsVlaues )
{
if($NetbiosOptionsVlaue.NetbiosOptions -ne 2)
{ $Counter+=1 }
}
if($Counter -eq 0) { Write-Output $true }
else { Write-Output $false }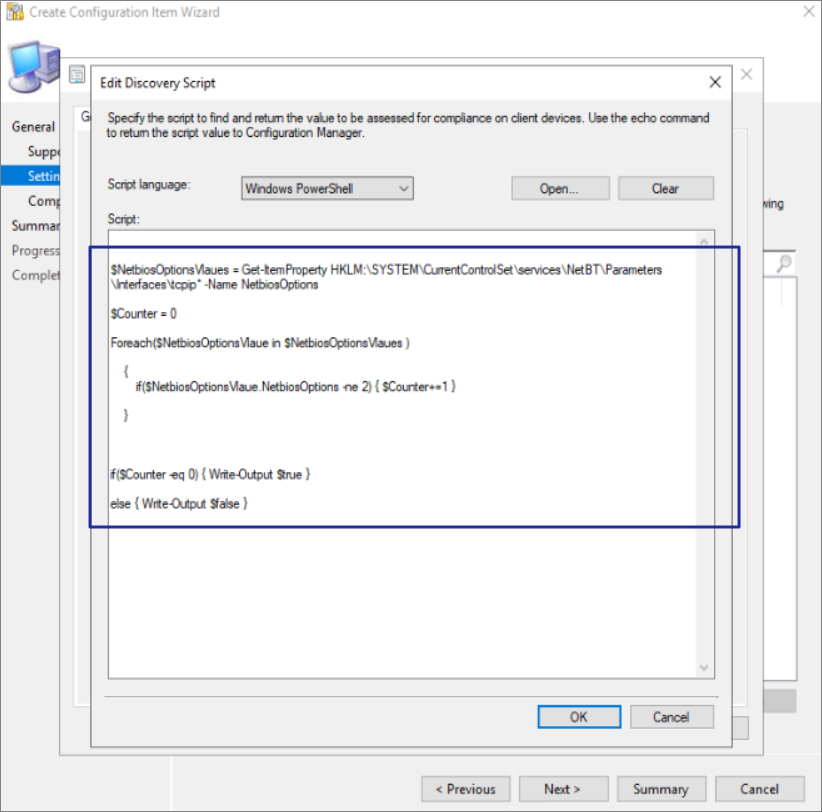


After deploying this application to collections, based “Schedule re-evaluation for deployments” client setting deployment of this application will be re-evaluated. In case evaluation returned as false then application will be re-enforced.
SCCM Configuration Item and baselines
Create a configuration item with following settings:
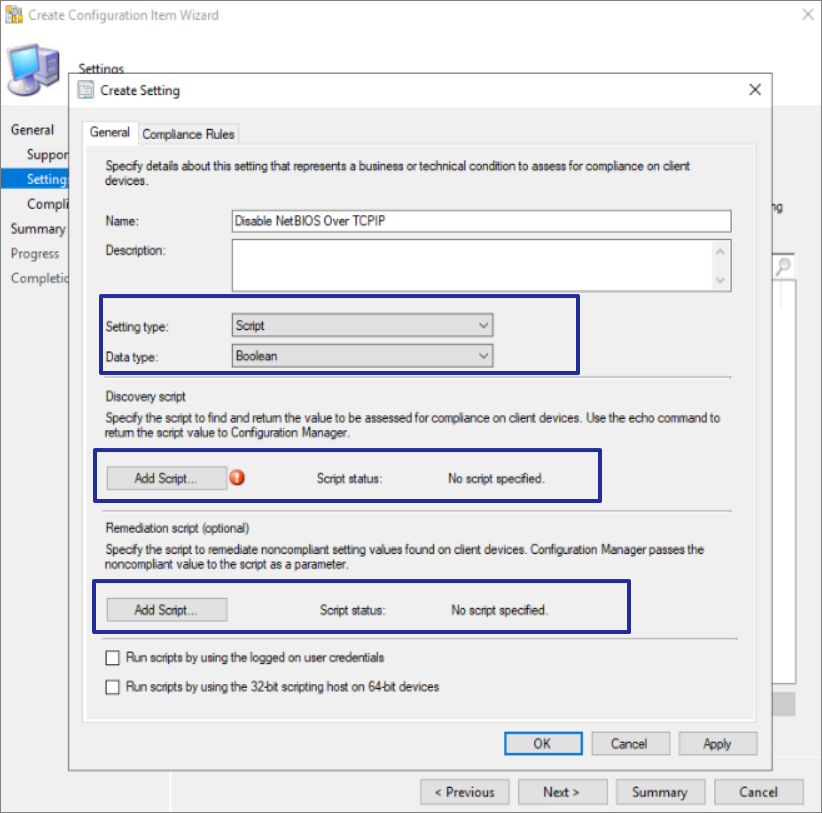


Script we used with SCCM application as detection rule, we will be using the same script as discovery script for configuration item.
$NetbiosOptionsVlaues = Get-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions
$Counter = 0
Foreach($NetbiosOptionsVlaue in $NetbiosOptionsVlaues )
{
if($NetbiosOptionsVlaue.NetbiosOptions -ne 2)
{ $Counter+=1 }
}
if($Counter -eq 0) { Write-Output $true }
else { Write-Output $false }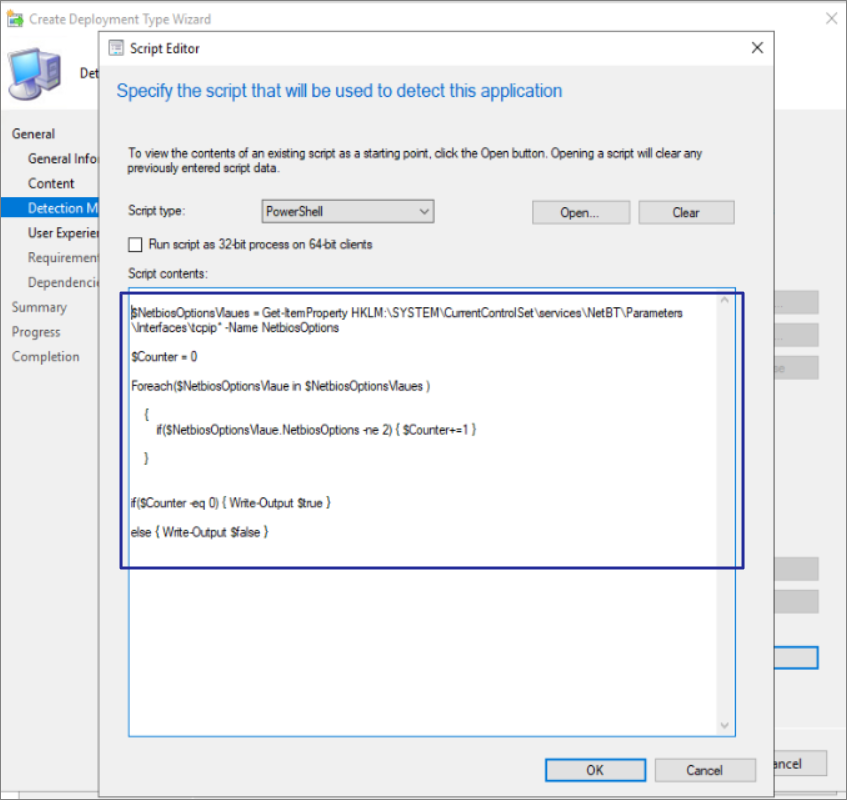


Remediation script will be the same script we used to set NetbiosOptions value to 2
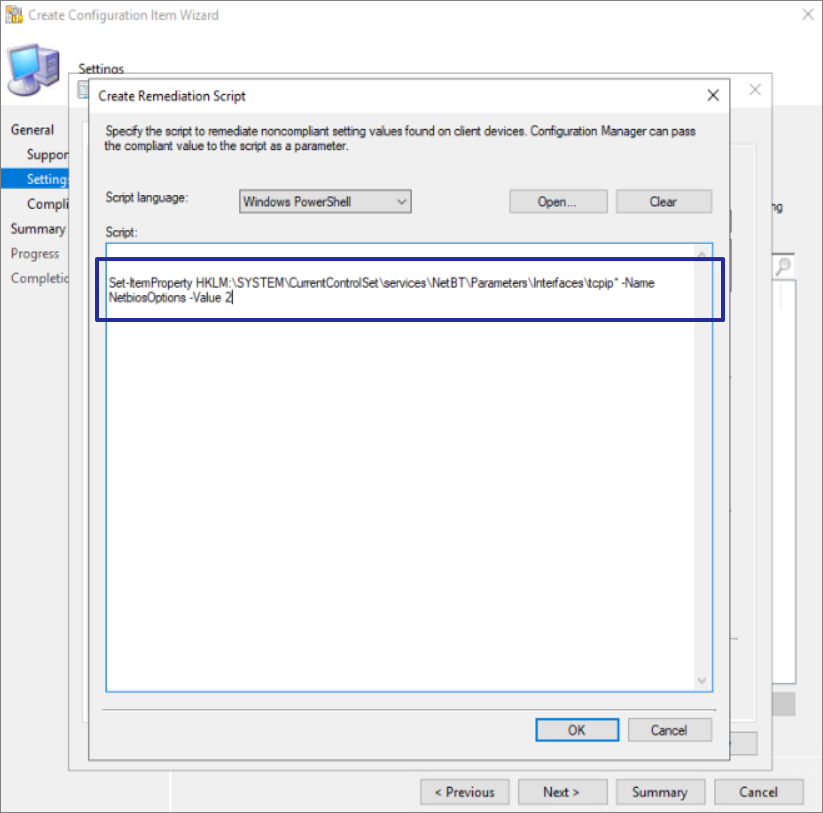


Next, create a configuration baseline which will be referring to earlier created configuration item as evaluation rule.
Make sure to check “Always apply this baseline even for co-managed clients”. This will ensure Baseline is applied to Co-Managed devices even though Device Configuration workload is delegated to Intune in Co-Managed scenario.



Click Add -> Configuration Item
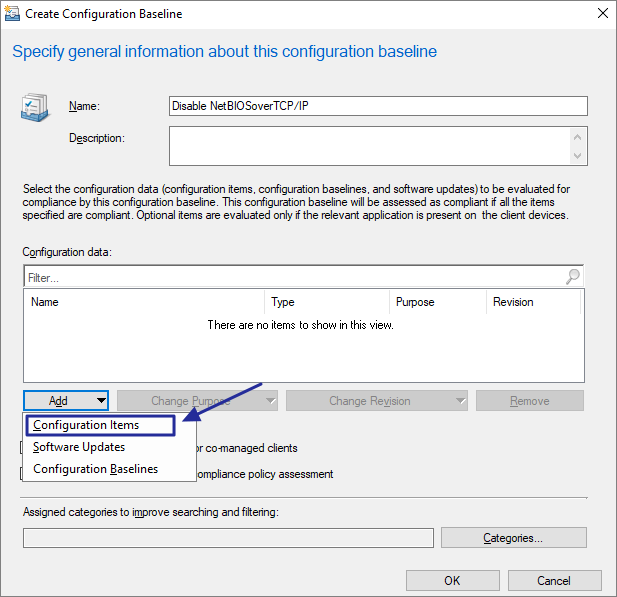





Deploy configuration Baseline to a collection, with following settings:
Enable Remediate noncompliant rules when supported
Enable Allow remediation outside the maintenance window Define evaluation schedule as per your requirement, best thing about configuration base line over SCCM application is that you can define evaluation schedule as per configuration baseline whereas an SCCM application relies on the evaluation schedule defined in the client policy which is applicable for all applications



Group Policy
Group policy has been around for quite a few decades helping administrators centrally managing the policies, settings, and configurations for Windows computers. Group policy also provide means of executing scripts, here are some methods to trigger remediation script via GPO.
Startup/Logon Scripts
Script to disable NetBIOS over TCP/IP can be achieved via Logon scripts, as the name suggests remediation script will be triggered at user logon or computer startup which will trigger the script. With this approach, any newly detected interface won’t get the NetBIOS setting unless device is restarted.
Here is an excellent article on how to use group policy logon/startup script.
Group Policy Preferences
Windows task scheduler is another method to execute remediation script at a scheduled, we can also define triggers for the same. This give administrator more control over execution of program/scripts, like running the script with highest privilege
Group Policy preferences can be used to create and deploy scheduled task to computers joined to the domain. This approach doesn’t require a restart in most of the cases, devices get the group policy at Group policy refresh cycle which is 90 minute by default.
Please refer Microsoft KB for more details about Task scheduler.
This is a great article on how to create task schedule via Group policy preferences and execute PowerShell.
Conclusion
Organizations nowadays have combinations of Azure AD joined, Hybrid AD Joined, Active Directory joined devices to be managed. Some devices always remain on the internet while others always or intermittently connect to corporate network. Considering this, administrators may have to go with a solution which is a combination of methods describes to disable NetBIOS over TCP/IP. Having said that, modern device management tools like SCCM and Intune give administrator more flexibility as device configuration can be pushed to the devices as they have internet connection, not matter they are on corporate network or public network.
I hope this post has been helpful to you. Please fee free to reach out if you have any further questions/comments/feedback.
Thank you.








Hi,
it looks good (I need to test it first ) thank you, I saw a typo error here:
DisableNetBIOSverTCPIP.cmd with following content to launch Uninstall_DisableNetBIOSverTCPIP.ps1
It should be Uninstall_DisableNetBIOSverTCPIP.cmd
Thanks
Hi Milena,
Thanks for taking the time to read this post and correcting me 🙂
Hi,
i tried following your steps and created the scripts, however if the created the scripts but they r not working i dont get any error.
if i type the commands in powershell directly it works perfect, what am i doing wrong
Best regards
Hi,
May I know which script and what is the method you are trying to deploy the script?
Thank you.
Hello. The Intune deployment works great (thank you) in deploying the setting but it reports Failure because of the Detection PS script. The PCs can’t run the Detection script because they are Restricted and there is no Bypass statement like the .Intune files include. I cannot figure out how to get around that. Any thoughts? Thank you.
Hi Keith,
Glad to know this post has been helpful for you.
You are correct, by default script execution is Restricted on Windows clients. First Set the execution policy to “AllSigned” on managed devices using group policy or Intune. Then use a signed PowerShell script for the Win32 App detection method. This will require efforts to set up but will make things easier for future deployments.
You may also set the execution policy to “Bypass” but this is not recommended.
I hope this helps.
Intune requires a STDOUT for detection scripts as well. It won’t take just the exit code.
Signing would be needed to, but without the stdout it sill won’t work.
if($Counter -eq 0) {
write-output “LLMNR Disabled”
exit 0
}
That’s what I changed the if statement to, to get it working on my end.
Thanks, Donato. Intune required both exit code 0 and data written to the STDOUT stream. I missed it earlier, I’ve added it to the Intune detection script now.
I tried the steps listed for Intune deployment and it did not work as i expected, something is not right, Deployment status failed on all test computers 100% failure
Any help will be much appreciated
Regards,
Hi,
What’s the error message? Please review IntuneManagedExtension.log to understand what might be causing this.